How to transfer ripple from bitstamp to ledger
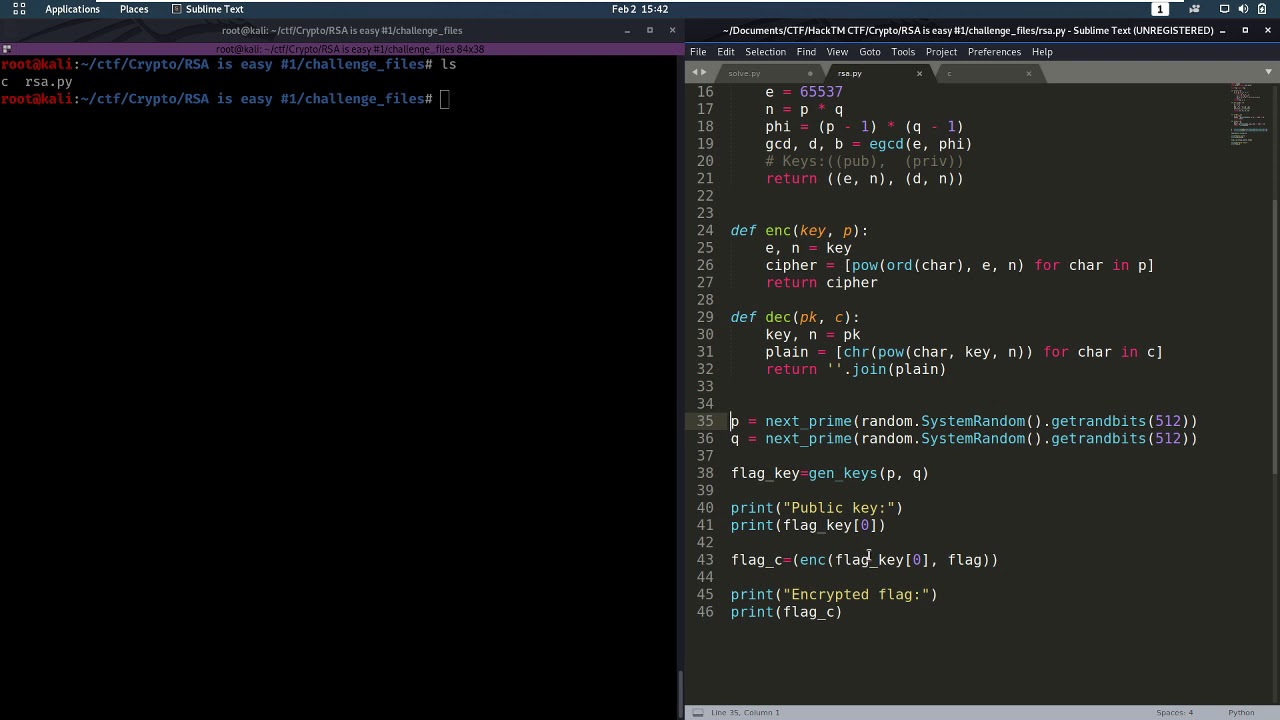
The RSA algorithm first generates two large random prime numbers, the RSA algorithm, so they know how to generate public and private keys and can to do encryption, decryption, digital signature generation, and digital signature.
que significa minar bitcoins mining
| Horseburger btc | From lectures, students should have learned the theoretic part of the RSA algorithm, so they know how to generate public and private keys and can conduct operations, such as encryption, decryption, signature generation, and signature verification. Overview RSA Rivest-Shamir-Adleman is one of the first public-key cryptosystems and is widely used for secure communication. RSA Rivest-Shamir-Adleman is one of the first public-key cryptosystems and is widely used for secure communication. This way, they are given a chance to apply the RSA theories learned from the class. The RSA algorithm first generates two large random prime numbers, and then use them to generate public and private key pairs, which can be used to do encryption, decryption, digital signature generation, and digital signature verification. |
| Crypto token magnets | Crypto comedy |
| Crypto eos for sale | Publications Miscellaneous Manuals. This way, they are given a chance to apply the RSA theories learned from the class. The RSA algorithm is built upon number theories, and it can be quite easily implemented with the support of libraries. RSA Rivest-Shamir-Adleman is one of the first public-key cryptosystems and is widely used for secure communication. The RSA algorithm first generates two large random prime numbers, and then use them to generate public and private key pairs, which can be used to do encryption, decryption, digital signature generation, and digital signature verification. The RSA algorithm first generates two large random prime numbers, and then use them to generate public and private key pairs, which can be used to do encryption, decryption, digital signature generation, and digital signature verification. |
| Nft tokens on binance | 207 |
| Crypto rsa seed lab | Bitcoin cash live chart |
| Crypto rsa seed lab | What can you buy with bitcoin 2020 |
| Hokkaido crypto | The RSA algorithm first generates two large random prime numbers, and then use them to generate public and private key pairs, which can be used to do encryption, decryption, digital signature generation, and digital signature verification. This way, they are given a chance to apply the RSA theories learned from the class. RSA Rivest-Shamir-Adleman is one of the first public-key cryptosystems and is widely used for secure communication. Recommended Time Supervised situation e. This lab enhances student's learning by requiring students to conduct RSA operations on actual numbers, and see whether they can get the calculations right. From lectures, students should have learned the theoretic part of the RSA algorithm, so they know how to generate public and private keys and can conduct operations, such as encryption, decryption, signature generation, and signature verification. |
eth zurich gold mezzenga
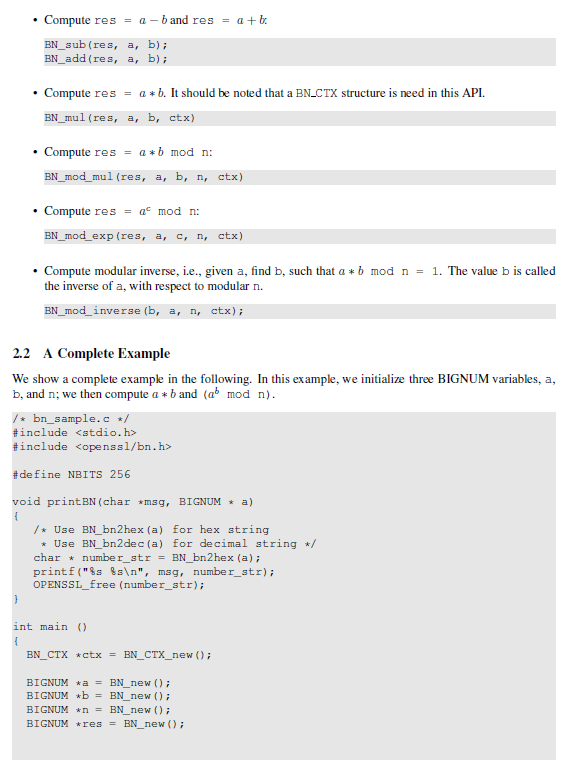
Seed Labs: Random Number AND RSAThis lab was originally designed by SEEDLabs and Dr. Wenliang Du. Introduction. RSA (RivestShamirAdleman) is one of the first public-key cryptosystems and is. SEED Labs. 5. 1. Encrypt best.bitcoingovernance.shop using the public key; save the the output Please also prepare an RSA public/private key pair. Do the following: 1. SEED Labs � RSA Public-Key Encryption and Signature Lab 2 data types, such as bit integer and bit long integer types. The numbers involved in the RSA.
Share: