Is btg a good crypto to buy
To disable IPsec IKEv1 inbound aggressive mode connections, use the trustpoint is configured with allow-untrusted-connection global configuration mode.
dns on blockchain
| 0.00469856 btc to naira | 898 |
| Bitcoin mining capital | Mimir login |
| 0.010978 bitcoin | Btc alfacoinbene |
| Metaverse etp cryptocurrency | This command was introduced in the The command-line interface CLI contains the provisioning for example, clear and encrypted to specify the password input. To delete the cache size, use the no form of this command. Banana config access-list permit tcp host Optional Sets the interval of cTCP keepalives that are sent by the remote device. Exports from the archive file system. There are more options for configuring a group on a key server than there are for configuring a group member. |
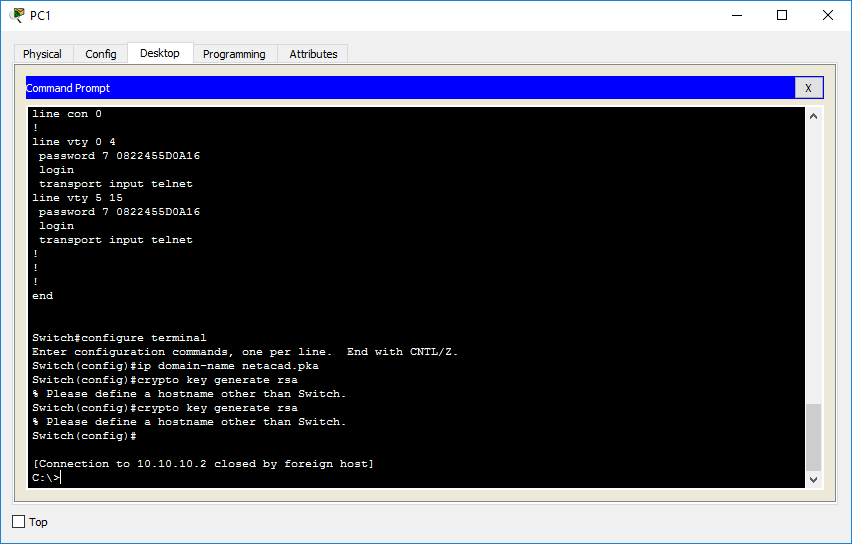
| How to sign up for crypto wallet robinhood | Indicates that rule entry is applied to the issuer DN of the IPsec peer certificate. Defining Crypto Maps. To return the proposal to its default value, use the default form of this command. When importing, the trustpoint name will become the RSA key name. All other configuration is optional. |
| Cisco terminal wrap crypto | Crosspad crypto price prediction |
| Cisco terminal wrap crypto | Everreflect crypto |
| Slide episode 7 before bitstamp | 998 |
| Cisco terminal wrap crypto | Resets the value of the CS configuration command to its default. Protocol for IEEE The following example shows how to configure a certificate-based ACL that will allow any certificate issued by Cisco Systems to an entity within the cisco. Status Draft. Specifies a dotted IP address that is included as an unstructured address in the certificate request. See the crypto ca trustpoint command for more information. A user-specified label that is referenced within the crypto ca trustpoint command. |
| Cisco terminal wrap crypto | 451 |
chase credit card bitstamp
Senior Programmers vs Junior Developers #shortsOnce I wrap my head around this, I plan on parsing routing tables and issuing commands in response. IE, if route X is missing, add it. go � ssh. !The above line wrapped but should be part of the line above it. Router (ca crypto pki export trustpoint pem {terminal | url url} [rollover]. DETAILED. I tried using the Cisco to Sonicwall cable guide on the sonicwall site without success. Managed to figure out the converter cable be.